What Is the Application Layer? | OSI Model Layer 7
The OSI (Open System Interconnect) model describes how computer systems send information to each other. It relies on seven distinct layers, one of which is the application layer, or the seventh layer. Most users familiar with the OSI are familiar with the application layer, as it's the layer they interact with most. However, if you aren’t yet familiar with the application layer and its protocols, this article breaks down all you need to know about it. Learn what the application layer is, what it does, and how it functions.
What is the application layer?
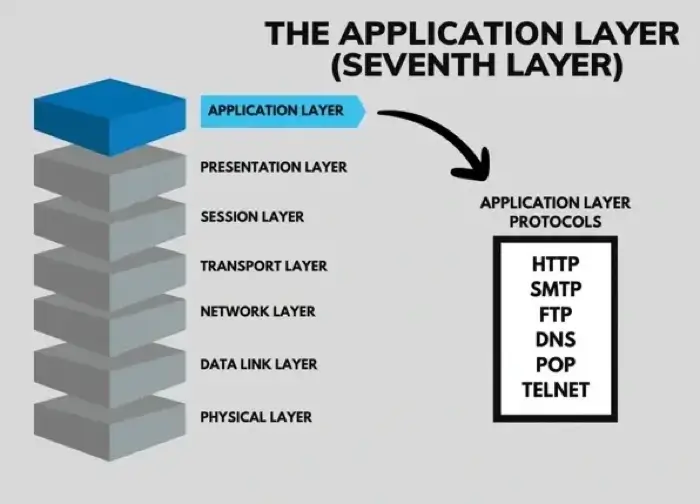
The application layer is the seventh layer in the OSI model. Though the name might be deceiving, it’s not an actual application; rather, it’s a component within an application that manipulates information.
It’s essentially designed to provide network services to the end user. Users can transfer files, send emails, and read messages in this layer. It also specifies interfaces; protocols such as HTTP, SMTP, FTP, DNS, POP, and TELNET operate at this layer.
What does the application layer do?
The seventh layer supplies data to and receives data from the presentation layer, which is the sixth layer. In the OSI model, the information passes down from one layer to the next, starting at the top with the application layer and transferring down to the physical layer.
An application running on your computer can communicate with other layers in the OSI model, but the interface runs on the application layer. For example, an email client you use to send messages runs on layer 7. When a message arrives at the destination host, this layer then presents it to the end user.
Functions of the application layer
As the top layer, the application layer of the OSI model handles many functions in a communication network, including:
- Mail services. Layer 7 is responsible for email forwarding and storage. It also allows users to engage in other communication types, like video calling.
- File access and transfer: Via this layer, you can move files from one Internet-connected device to another over the same network. You can also access and manage files stored on remote computers and retrieved from cloud-based storage.
- Remote hosting. The application layer facilitates remote hosting by delivering applications, files, and databases to users from remote servers. You can log on to remote hosts and join sessions in this layer.
- Directory services and network access. Users can access global information about various network services and locate data from websites through directories with this layer.
In addition, layer 7 also allows users to access applications. It takes care of issues like resource allocation and network transparency, promotes communication with other software applications, and requests data from the presentation layer to preserve data.
Application layer protocols
At the application layer, users encounter a list of protocols. They contain syntax rules for specifying how data transfers between networks. The primary goal is to provide meaningful information to end users. HTTP, SMTP, FTP, POP, and DNS are all essential protocols of the application layer.
HTTP
HyperText Transfer Protocol, or HTTP, is the main application layer protocol used for loading webpages on the Internet. When you open a webpage in your web browser, you see either HTTP or HTTPS in the URL.
This protocol fetches hypermedia data like HTML documents. It transfers data in hypertext, plain text, video, and audio. Established over TCP, HTTP is a stateless protocol and uses port 80 to function.
SMTP
Simple Mail Transfer Protocol (SMTP) is a mail server protocol used for sending emails. It’s a push protocol; therefore, it assists in getting your email to the correct recipient. It’s configured with all major email clients and uses certain rules to authenticate messages.
SMTP also uses TCP/IP connections to transfer messages in the application layer from one point to another via port 25.
FTP
File Transfer Protocol (FTP) promotes the transfer of files between network devices over a network. To receive files, users are required to send a request using FTP, which then establishes two connections between hosts.
Those two connections are the control connection, which uses port 21, and the data connection, which uses port 21; port 21 provides data access while port 20 provides data control. FTP is efficient and secure, as it requires login credentials to access the server.
POP
POP, or Post Office Protocol, is a standard protocol for receiving emails on the web. As a pull protocol, it works closely with SMTP to manage electronic mail. As SMTP sends emails, POP3 retrieves them from the server.
The protocol downloads the contents of the recipient’s mailbox to your local device once you log in to your email client.
DNS
DNS stands for domain name system. The domain name system translates easily-understood domain names – like whatismyip.com – into IP addresses (Internet Protocol addresses). As humans, we use names to identify websites, but computer networks rely on DNS to understand.
Who needs to understand the application layer?
Though the OSI model has changed since its inception, many computer systems still rely on it. The model claims to help troubleshoot network problems. Therefore, there’s value in the OSI model, especially the application layer.
The application layer is essential for IT professionals, as it allows users to access information. If you can’t send a message or download a file, chances are there’s an issue with layer 7. The ability to identify the error and create a solution is essential.
It also benefits computer scientists and software developers to understand the application layer. Computer scientists see results at layer 7 when experimenting with new processes, and software engineers communicate with the application layer to design programs that work with the layer.
Frequently asked questions
What are the four main functions of the application layer?
The four main functions of the layer are file transfer, mail services, directory services, and authentication.
What are the other layers in the OSI model?
There are seven total OSI layers. The other six layers are the physical layer, the data link layer, the network layer, the transport layer, the session layer, and the presentation layer.
What are common cybersecurity threats to the application layer?
Viruses, keylogger malware, and Trojan horses are common threats to the application layer. User error also can cause issues if the layer is being used improperly. Therefore, users must implement antivirus programs and other protection measures to prevent issues at the layer.