ARP Poisoning | What Is ARP Cache Poisoning?
Cyber attackers use many tactics, including malicious attacks, email phishing, password attacks, and ARP poisoning, to breach even the most fortified systems. ARP spoofing is a cyber attack where an attacker sends false ARP messages on a local area network (LAN), resulting in ARP cache poisoning. In this article, learn what ARP poisoning is, how it works, and how to prevent it.
What is ARP poisoning?
ARP poisoning is a type of cyberattack that exploits the Address Resolution Protocol (ARP) in a local network. The goal is to trick devices into thinking the attacker’s MAC address belongs to a legitimate IP address, like that of the network gateway or another trusted device. As a result, data intended for the actual device goes to the attacker instead.
ARP, or Address Resolution Protocol, is key to network communication. It links IP addresses at the network layer to MAC addresses at the data link layer so devices can identify each other on a network. When a match between an IP and MAC address is found, the device successfully connects to the Internet.
Many applications store these matches temporarily in a cache to improve efficiency. If a match isn’t known, the application sends out an ARP request to discover the correct IP and MAC pairing.
The ARP protocol is designed for connection purposes. So ARP lacks built-in security measures because it doesn’t confirm if a response is from a trusted source. It also allows devices to accept ARP replies even without a sent request. These vulnerabilities make ARP susceptible to cyber threats.
ARP is limited to the older IPv4 system that uses 32-bit IP addresses. The new IPv6 system replaces ARP with the Neighbor Discovery Protocol (NDP). NDP relies on cryptographic keys to verify devices. However, because IPv4 is still widely used, ARP remains helpful in many networks.
The cache poisoning attack enables cyber criminals to intercept communication between devices on a network. They achieve this by corrupting the ARP tables of devices with false information. An ARP table is simply a record maintained by a device on a local network.
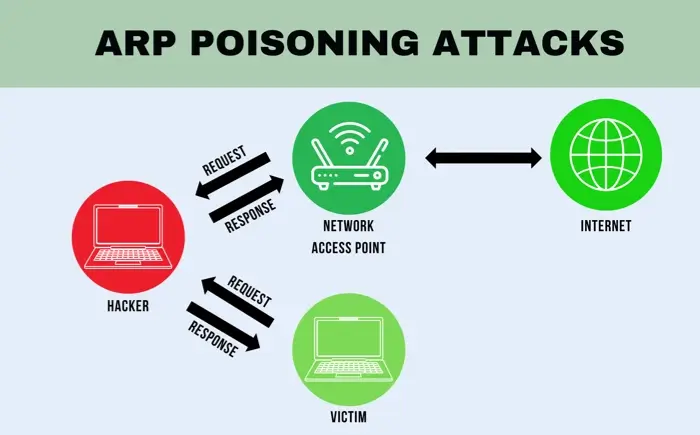
How ARP poisoning works
An ARP poisoning attack is carried out over a local area network. It involves abusing the weaknesses in ARP to manipulate the MAC-to-IP mappings of other devices on the network. The attack works as follows:
- Selecting the target. The attacker identifies a target for the attack first. This could be a specific device, a group of devices, or a critical network component like a router. Routers are particularly appealing targets because compromising them can disrupt communication for all devices connected to that subnet.
- Initiating the attack with tools. The attacker uses specialized tools that allow the attacker to craft and send fake ARP messages. They might immediately flood the network with fake ARP responses to overwrite ARP caches or wait for legitimate ARP requests to send malicious responses in real time.
- Exploiting redirected traffic. Once the attacker corrupts the victim’s ARP cache, the attacker takes advantage of the rerouted traffic. The action depends on their ultimate goal, such as intercepting sensitive information.
Following a successful ARP cache poisoning attack, the attacker can do any of the following:
- Intercept traffic. They monitor the traffic to capture sensitive information like passwords or personal data.
- Alter data. Attackers modify the data before it reaches its destination.
- Disrupt the network. They drop the traffic entirely, causing communication failures and network outages.
The attacker’s actions depend on their intentions, whether data theft, sabotage, or network manipulation.
Types of ARP poisoning attacks
Once attackers gain access to a network through ARP poisoning, they hijack all communications and exploit the system further. Here are the main types of attacks they can launch.
Distributed denial-of-service (DDoS) attacks
Attackers use ARP poisoning to overwhelm a system by directing excessive traffic to it. ARP’s function of connecting IP addresses to MAC addresses is exploited to route large volumes of data to a specific application.
This flood of traffic exceeds the system’s capacity, causing it to crash or become unresponsive. Essentially, the attacker bombards the target with requests it cannot handle to disrupt services.
Session hijacking attacks
With ARP cache poisoning, attackers can monitor all network communications and steal session IDs, which are critical in maintaining user authentication across applications.
The objective is to impersonate users, access their accounts, and perform unauthorized actions. Victims remain unaware as the attacker exploits their ongoing authenticated sessions.
SQL injection attacks
Attackers use ARP poisoning as an entry point to control critical application features. They then launch SQL injection attacks, injecting malicious code into the application’s database.
Such an attack corrupts database queries, allowing attackers to alter HTTP requests, steal sensitive data, or even rewrite entire sections of a website. This creates opportunities for attackers to compromise data integrity.
Man-in-the-middle (MiTM) attacks
In MiTM attacks, the attacker inserts themselves between two communicating parties, such as users or applications, and reroutes network traffic through their own system.
From this position, they can monitor conversations, steal sensitive data, and even inject malware into the communication stream. This attack allows threat actors to exploit conversations without the users noticing any unusual activity.
Consequences of ARP spoofing attacks on cyber security
The effects of ARP spoofing go beyond minor disruptions. They pose serious threats to individuals and organizations. The damage caused, such as stolen data, connectivity issues, and financial losses, can be difficult to recover fully.
Data theft
One of the most dangerous outcomes of ARP spoofing is the theft of sensitive data. Attackers can intercept login credentials, passwords, financial details, and private messages.
If the network is unencrypted, stolen information becomes even more vulnerable. For businesses, this results in the exposure of proprietary data, leading to a loss of customer trust.
Network disruption
ARP spoofing corrupts ARP tables to cause disruptions within a network. These actions can result in slow system performance, complete outages, or denial-of-service (DoS) attacks.
The downtime caused by these disruptions leads to operational inefficiencies for businesses. In some cases, interrupted essential services impact customers.
Malware distribution
Attackers often use ARP spoofing to inject malicious code into the network. Once malware is introduced, it can quickly spread to other systems.
Once infected, recovering the network becomes costly. Malware distribution remains undetected until significant damage occurs.
How to detect ARP poisoning on your network
Detecting ARP poisoning can be difficult due to the lack of a verification process in the ARP protocol. ARP entries are automatically cached and updated without authentication, so attackers can easily manipulate them.
However, careful observation helps identify suspicious activity. Here are effective detection methods:
ARP monitoring
Consistent tracking of ARP traffic is crucial to spot irregularities. Network administrators can observe ARP packets to detect anomalies, such as multiple MAC addresses receiving assignments to the same IP address.
This kind of mismatch is a strong indicator of ARP spoofing. Monitoring tools can automate this process and send alerts in real time when a network detects suspicious activity.
Gratuitous ARP detection
Gratuitous ARP packets are unsolicited ARP reply devices share to declare their IP-MAC mapping. A sudden surge in these messages often signals ARP poisoning.
Monitoring tools can track the frequency of gratuitous ARP packets. A spike in their volume should prompt further investigation as it might reveal an ongoing attack.
Traffic analysis
Unusual traffic patterns can be a clear sign of ARP poisoning. Administrators can identify discrepancies, such as unexpected traffic volumes, by analyzing the flow of data.
For instance, if a device starts receiving traffic from multiple sources without explanation, it could indicate that its connection is being intercepted. Intrusion detection systems (IDS) can flag abnormal traffic patterns for review.
Detecting duplicate MAC addresses
Duplicate MAC addresses on a network are another warning sign. Attackers frequently use spoofed MAC addresses to redirect traffic that creates duplicates in the network.
Tools such as Nmap or dedicated ARP monitoring software can scan the network to identify these duplicates on time and alert administrators to potential spoofing.
Using security solutions
Advanced security systems like intrusion detection systems (IDS) and intrusion prevention systems (IPS) are impactful in identifying ARP poisoning. These tools analyze traffic patterns, detect malicious activities, and block suspicious behavior before it impacts the network.
How to prevent ARP poisoning
Organizations can adopt various strategies to minimize the risk of ARP poisoning. Implementing a mix of technical measures, network configurations, and awareness practices can significantly enhance protection.
- Employ dynamic ARP inspection (DAI). Dynamic ARP Inspection is a feature available on some network switches that examines ARP packets before allowing them to pass through the network. It verifies the authenticity of ARP requests, stopping attackers from injecting malicious entries into ARP tables.
- Set up static ARP entries. Manually assigning static ARP entries for critical devices, such as routers and servers, can prevent unauthorized modifications to ARP caches. This method ensures that only approved MAC and IP pairings are used. While effective for small networks, it may not be practical in larger or frequently changing environments.
- Use network segmentation. Dividing the network into smaller, isolated segments limits the reach of ARP poisoning attacks. If an attack occurs in one segment, it cannot easily spread to other network parts. This approach enhances overall security by containing potential threats.
- Implement 802.1X authentication. The 802.1X protocol enforces port-based access control by requiring devices to authenticate before gaining access to the network. This ensures that only trusted devices can connect.
- Update security software regularly. Keeping security tools, operating systems, and firmware up to date is essential. Updates address vulnerabilities that attackers could exploit to provide an additional layer of defense against ARP poisoning.
- Provide Security Awareness Training. Educating employees about ARP poisoning and other cyber threats can significantly reduce risks. Awareness programs can teach users to follow security best practices to recognize suspicious activity.
ARP poisoning vs. ARP spoofing
Although the terms ARP spoofing and ARP poisoning often work together, they differ slightly in scope. ARP spoofing refers to the general act of sending fake ARP messages to associate a malicious MAC address with a legitimate IP address. It serves as the method used to deceive devices on a network.
ARP poisoning, meaning the specific outcome of ARP spoofing, is slightly different. It occurs when the ARP cache of one or more devices is corrupted with false entries.
Frequently asked questions
Is ARP poisoning limited to specific networks?
ARP poisoning only affects IPv4 networks because it relies on the ARP protocol used in IPv4.
Why is ARP vulnerable to attacks?
ARP was not designed with security in mind. It lacks authentication for ARP responses, allowing attackers to easily forge ARP messages and corrupt ARP caches.

